Was There Foreign Interference In This Election? You Make The Call.
By Patrick Byrne
CreativeDestructionMedia.com

The occasion was a 1950’s drunken Hollywood party. The leading men of the day were holding a certain impromptu contest. Jackie Gleason famously shouted out a request to Milton Berle: “Hey Miltie, do us all a favor, and only pull out enough to win!”
In this chapter I will follow that principle. I shall start with an analysis of the packet traffic on Election Day 2020. As packets travel through the Internet they leave a trail, and dolphin-speakers using the right tools can, in a sense, “shine a light” and reveal those packet trails in the cyber-fog. Here is a video of only 1 minute which shows hundreds of foreign entities (many in China) who, on November 3, 2020, were hitting voting machines across Pennsylvania, Michigan, Wisconsin, Arizona, Nevada, and Georgia.
(Scroll down)
raw from David Martin on Vimeo.
Now let us turn to a statement by a retired senior military officer that lays things out rather clearly (there is a fair bit of “dolphin-speak” below, but if you read it slowly, most will make more sense to you than you may expect).
———————————————————————————————————–
Declaration of XXXXXXXX
1. My name is XXXXXXXXXXXXXXXXXXXX, and I am a resident of XXXXXXXXXX. I hold an MBA from XXXXXX University, and a Bachelor of Science from XXXXXX University. I am retired from the US Army where I worked as an Air Cavalry Officer, a Psychological Operations Officer, and Information Operations Officer. I specifically conducted Special Technical Operations, analyzed and applied All-Source Intelligence to operational requirements. With a specialized team of military members, I helped author the Joint Urgency of Needs Statement for the CAUI EXORD (Countering Adversary Use of the Internet) and stood up the first two special category cyber-enabled operations under a unique Secretary of Defense authority. I am currently the manager of a Cybersecurity Company based in Texas. Our emphasis is on digital forensics and incident response (DFIR) cybersecurity, analysis of publicly available information (PAI), penetration testing of networks, and problem solving through operations integration. We use state-of-the-art tools and employ a wide variety of cyber and cyber-forensic analysts. My colleague and I are currently contracted to a cybersecurity and forensics firm that focuses on election systems.
2. We have examined the various Companies, Networks, Structures, Machines and related global infrastructures directly tied to the US Election.
3. This is a preliminary report on the various aspects of FOREIGN INTERFERENCE as defined by Executive Order 13848 issued on September 12, 2018.
a. Section 8 (f) defines the term “foreign interference,” with respect to an election, to include any covert, fraudulent, deceptive, or unlawful actions or attempted actions of a foreign government, or of any person acting as an agent of or on behalf of a foreign government, undertaken with the purpose or effect of influencing, undermining confidence in, or altering the result or reported result of, the election, or undermining public confidence in election processes or institutions.
i. There is clear and definitive evidence that foreign interference, as defined in the above Executive Order, occurred prior to, and during, the General Election on November 3, 2020.
b. In addition, Section 1 (b)(ii) states “if any foreign interference involved activities targeting the infrastructure of, or pertaining to, a political organization, campaign, or candidate, the extent to which such activities materially affected the security or integrity of that infrastructure, including by unauthorized access to, disclosure or threatened disclosure of, or alteration or falsification of, information or data.”
i. There is also clear and definitive evidence that foreign interference and unauthorized access to information and data, as defined in the Executive Order above, occurred prior to, and during, the General Election on November 3, 2020.
Dominion Voting Systems and Scytl/Clarity Elections:
4. Dominion Voting Systems is owned and controlled by foreign entities. We lose control of the data when it goes to a foreign country. For example:
• The electronic information went to Germany, Barcelona, Serbia, and Canada
• Dominion Servers in Belgrade Serbia. P 82.117.198.54 (ASN Range: 82.117.192.0/19)
• Dominion Servers ftp.dominionvoting.com with IP 69.172.237.100 (ASN Range: 69.172.236.0/22) is located in Toronto, Canada
• www.scytl.com with IP 52.57.209.147 (ASN Range: 52.57.0.0/16) is (was) located in Frankfurt Germany
• support.scytl.com with IP 213.27.248.118 (ASN Range: 213.27.128.0/17) is located in Barcelona, Spain
• scytl-com.mail.protection.outlook.com with IP 104.47.10.36 (ASN Range: 104.40.0.0/13) is located in Ireland
• On election night the DE-CIX Frankfurt there was a 30% spike over the previous high rate of traffic. One stated probable cause was increased data flow to servers supporting the US Election.
Dominion Voting Systems and related companies are owned or heavily controlled and influenced by foreign agents, countries, and interests. The forensic report we prepared found that “the Dominion Voting System is intentionally and purposefully designed with inherent errors to create systemic fraud and influence election results”.
5. The system intentionally generates an enormously high number of ballot errors…The intentional errors lead to bulk adjudication of ballots with no oversight, no transparency, and no audit trail. This is the exact type of issue that leads to voter and/or election fraud.
6. The report found the election management system to be wrought with unacceptable vulnerabilities— including access to the internet— a key indicator to find evidence of fraud, and numerous malicious actions.
7. The numerous similarities will find that Dominion Voting Systems, Smartmatic, Electronic Systems & Software, and Hart Inter Civic, Clarity Election Night Reporting, Edison Research, Sequoia, Scytl, and similar or related entities, agents or assigns, have the same flaws and were subject to foreign interference in the 2020 election in the United States.
8. These systems bear the same crucial code “features” and defects that allowed the same outside and foreign interference in our election, in which there is the probability votes were in fact altered and manipulated contrary to the will of the voters.
a) Each of the companies use EML (Election Markup Language) and are susceptible to cross site scripting attacks (XSS) as described on page 7 in the Joint Cybersecurity Advisory.
i) Cross-site scripting (also known as XSS) is a web security vulnerability that allows an attacker to compromise the interactions that users have with a vulnerable application. It allows an attacker to circumvent the same origin policy, which is designed to segregate different websites from each other. Cross-site scripting vulnerabilities normally allow an attacker to masquerade as a victim user, to carry out any actions that the user is able to perform, and to access any of the user’s data. If the victim user has privileged access within the application, then the attacker might be able to gain full control over all of the application’s functionality and data.
b) Most, if not all, related sites were created using WordPress. WordPress currently has 2,675 CVE (Common Vulnerabilities and Exposures) listed on cve.mitre.org.
i) I performed a OpenVAS Vulnerability assessment for both Dominion and Scytl. There were multiple issues related to, out-of-date plugins and themes, which leaves sites vulnerable to attack.
c) With the various mergers, acquisitions, license agreements and partnerships the entire Election ecosystem in the United States is one and the same of any other Country where these systems are based, created, designed, used and so on. Namely Venezuela and their investment into Smartmatic.
d) Dominion’s purchase of Sequoia Voting Systems from Smartmatic has resulted in the same “Source Code” being used today.
e) During the Forensic audit we observed WinEDs and GEMS in the Dominion Voting System EMS (Election Management System). Both of those modules have been included in adverse findings from the EAC but are still in use today.
f) With the overlap between Dominion and Smartmatic, including the shared address in Barbados, the FCC Report ID: 2AGVK-VIU811 issued by the CCIS Lab in Shenzhen, China is very concerning. The Voter Identification Unit report was issued on July 23, 2020 and would give China insight on how to exploit the voting machines used in the US Election.
9. Dominion Voting Systems is based in Toronto, Canada, and assigns its intellectual property including patents on its firmware and software and trademarks to Hong Kong and Shanghai Bank Corporation (HSBC), a bank with its foundation in China and its current headquarters in London, United Kingdom.
10. Multiple expert witnesses and cyber experts identified acts of foreign interference in the election prior to November 3, 2020 and continued in the following weeks. In fact, there is evidence of a massive cyber-attack by foreign interests on our crucial national infrastructure surrounding our election—not the least of which was the hacking of the voter registration system by Iran. (E.O. 13800 of May 11, 2017)
11. This is compounded by the magnitude of the Solar Winds exploit that has exposed the private, public and government related companies and agencies. This includes the companies and agencies directly involved with securing our elections.
12. The FBI and CISA issued a joint Cybersecurity Advisory on October 30, 2020 (Report ID: AA20-304A).
a. This joint cybersecurity advisory was coauthored by the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI). CISA and the FBI are aware of an Iranian advanced persistent threat (APT) actor targeting U.S. state websites—to include election websites. CISA and the FBI assess this actor is responsible for the mass dissemination of voter intimidation emails to U.S. citizens and the dissemination of U.S. election-related disinformation in mid-October 2020.1 (Reference FBI FLASH message ME-000138-TT, disseminated October 29, 2020). Further evaluation by CISA and the FBI has identified the targeting of U.S. state election websites was an intentional effort to influence and interfere with the 2020 U.S. presidential election.
13. Dominion and Smartmatic share a physical address in Barbados despite their insistence that there is no relationship between the companies. They also have a mutual non- compete agreement detailing shared resources and code.
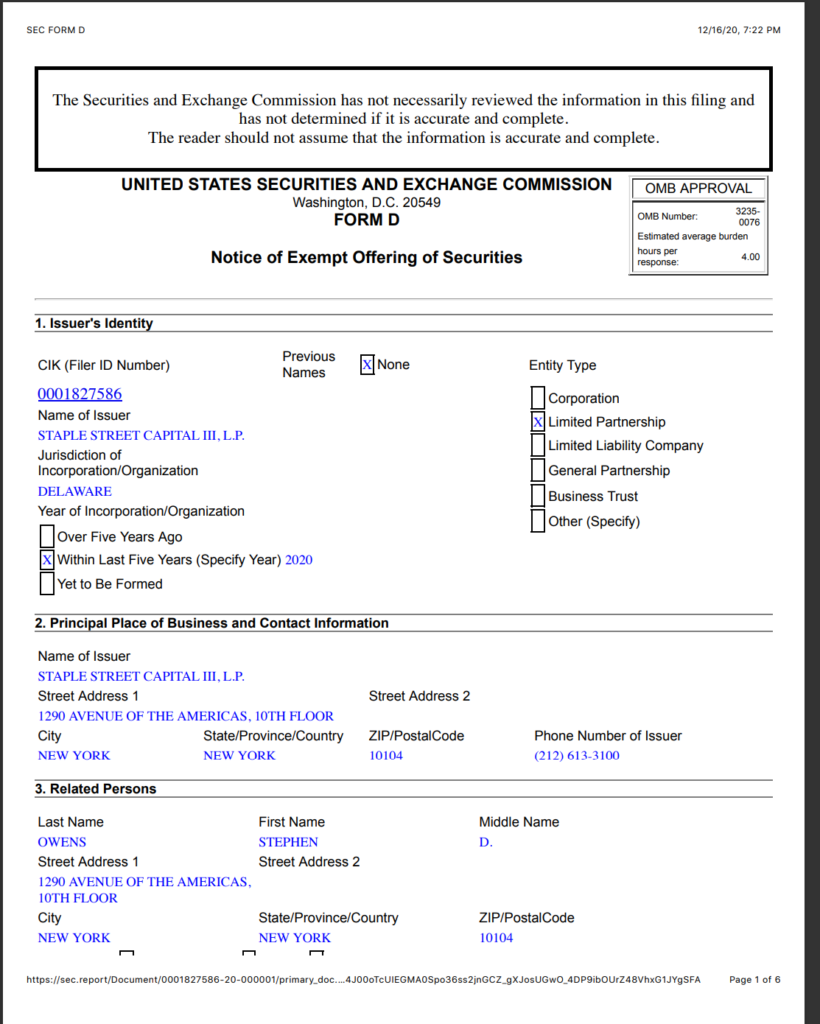
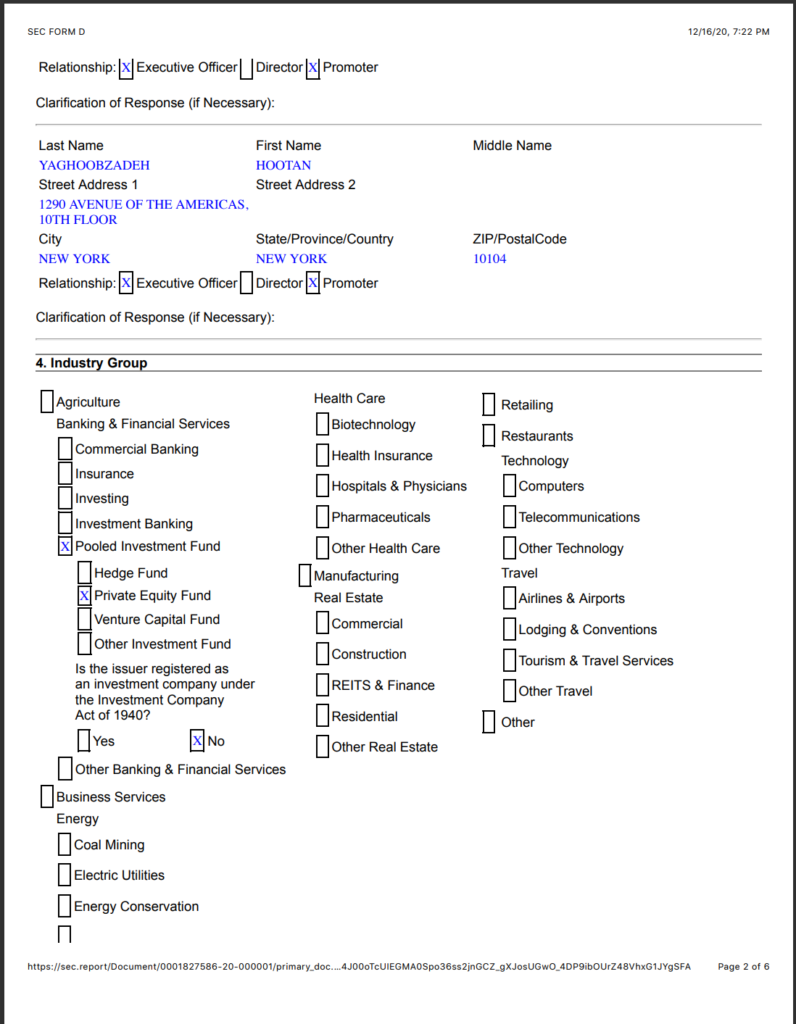
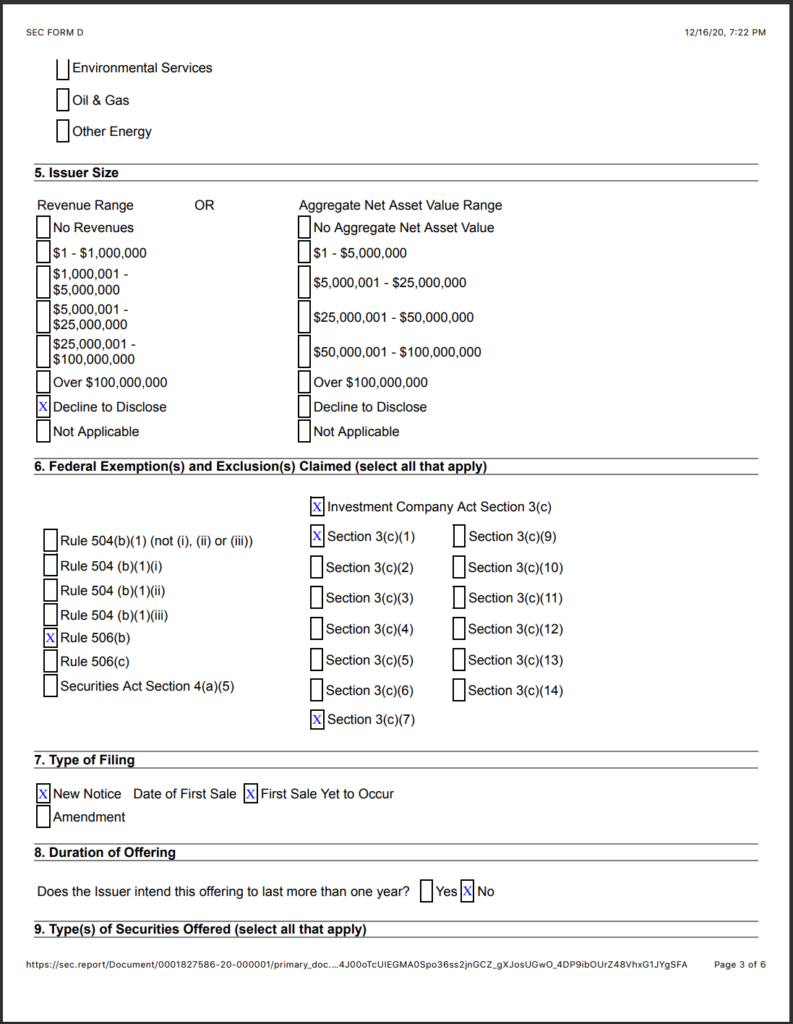
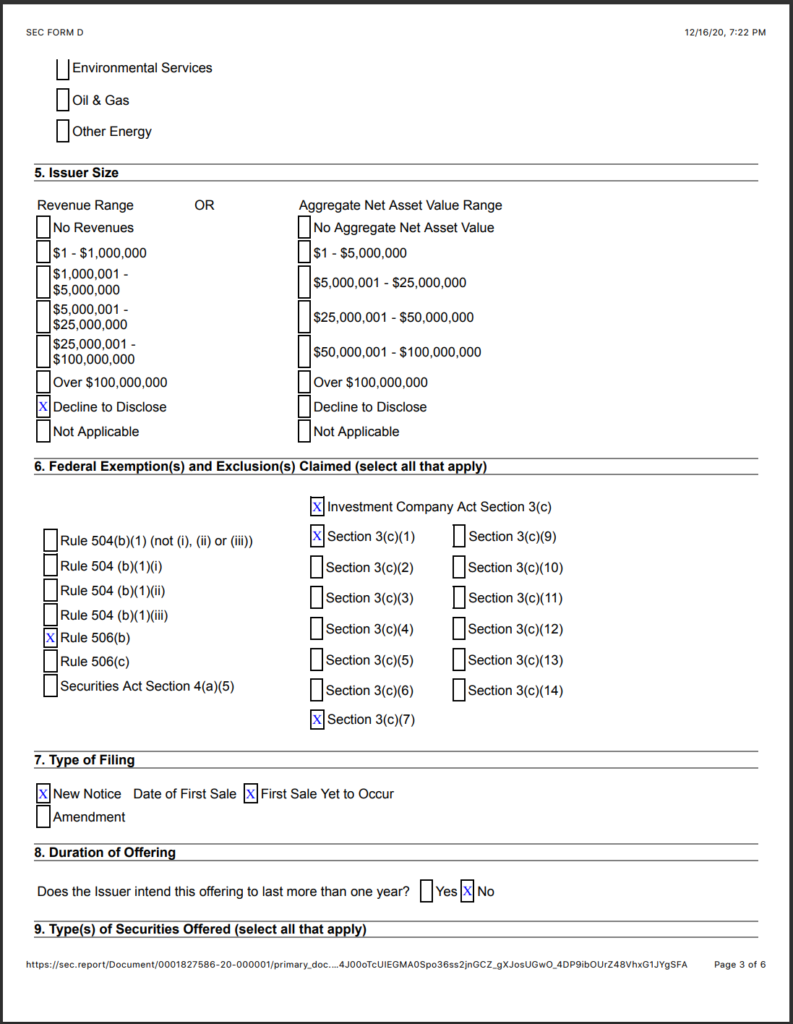
14. Hootan Yaghoobzadeh is the CEO and Chairman of Staple Street Capital, which is the entity that owns Dominion. Yaghoobzadeh was a close confidant to Sadaam Hussein and worked for the Saudi Bin Laden group. He previously worked at the Carlyle Group and Cerberus Capital Management.
Staple Street Partners
15. Staple Street Partners is a Private Equity firm that owns Dominion Voting Systems.
16. 9/25/19 – Dominion Voting Systems based in Toronto entered into a Security Agreement with HSBC Bank, assigning all intellectual property and assets including Trademarks, Patents and Software (see below).
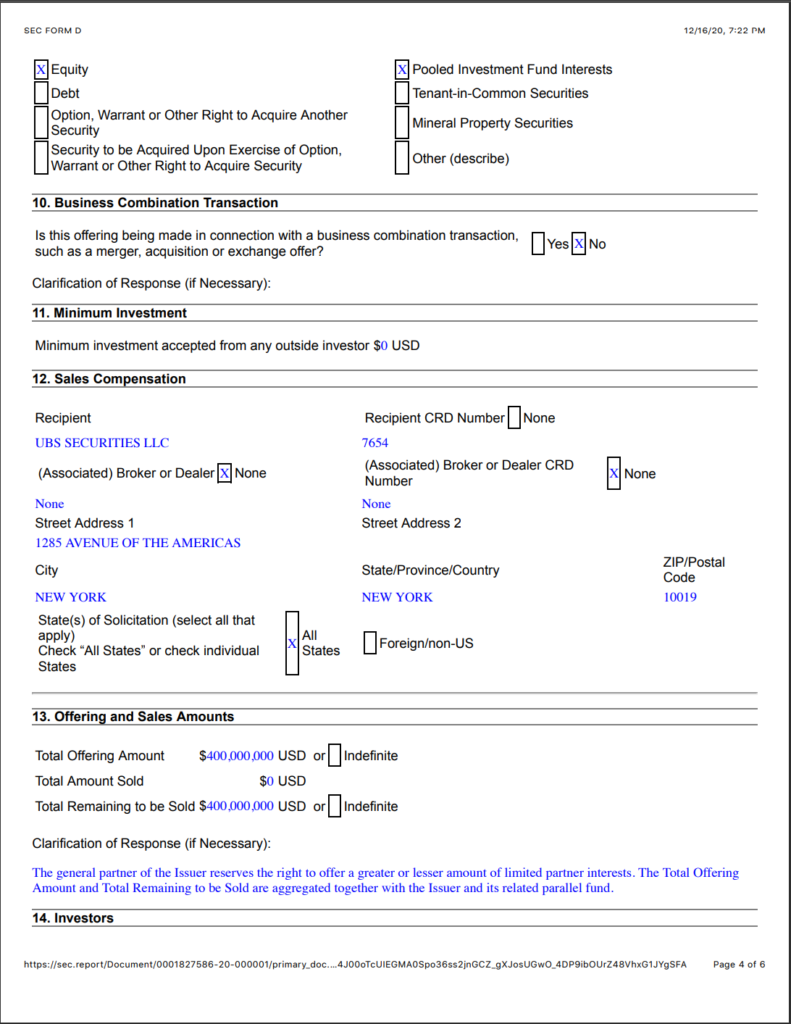
17. 10/8/20 – $400,000,000 from UBS Securities a Chinese managed subsidiary of UBS Global AG (see below).
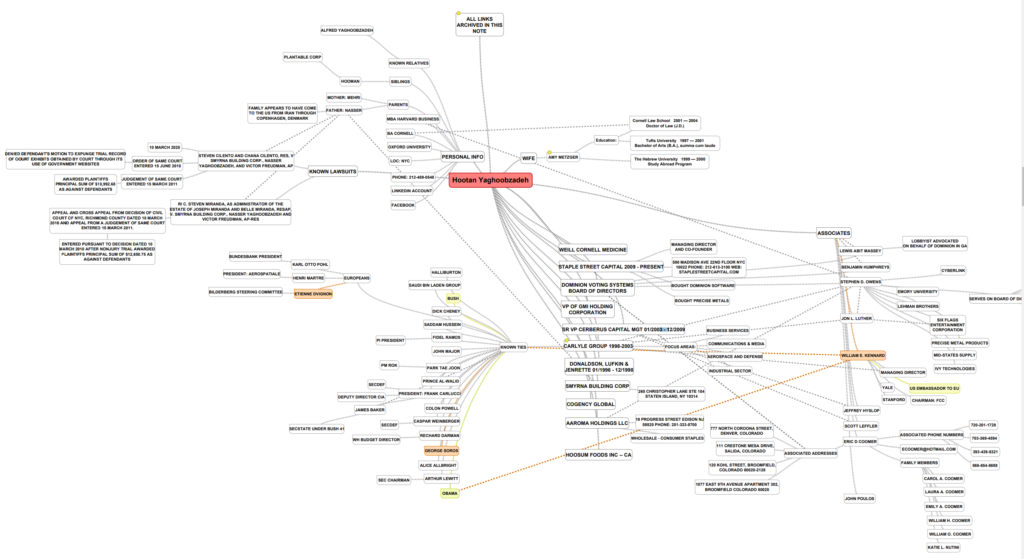
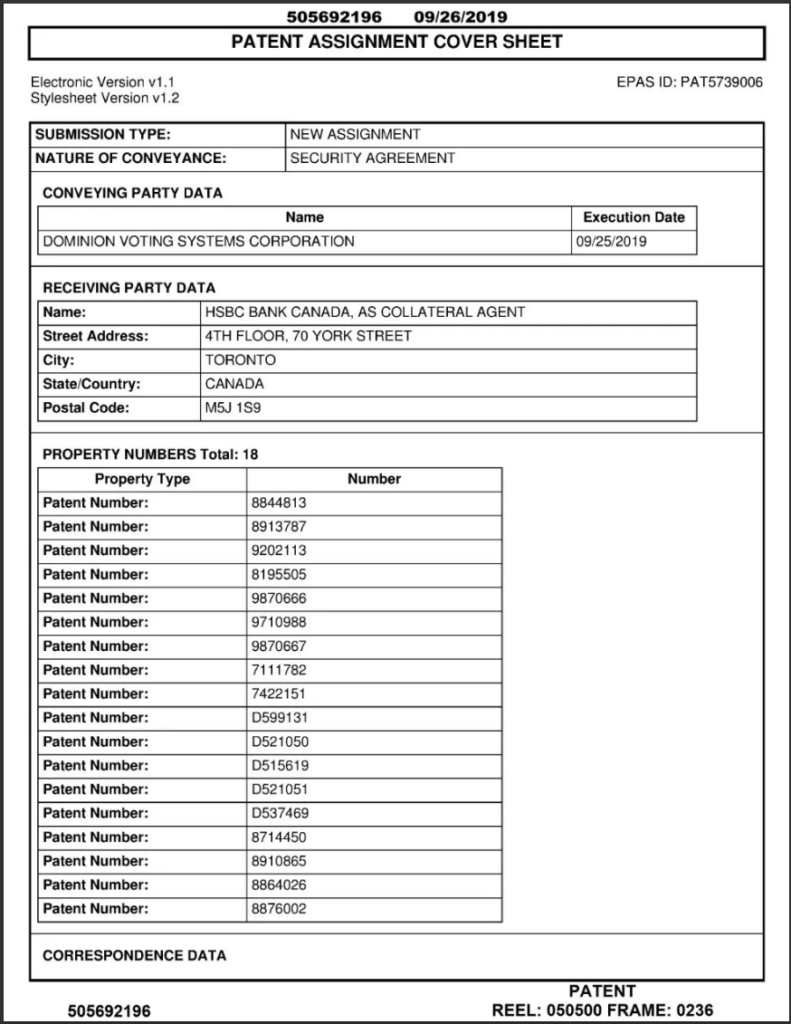
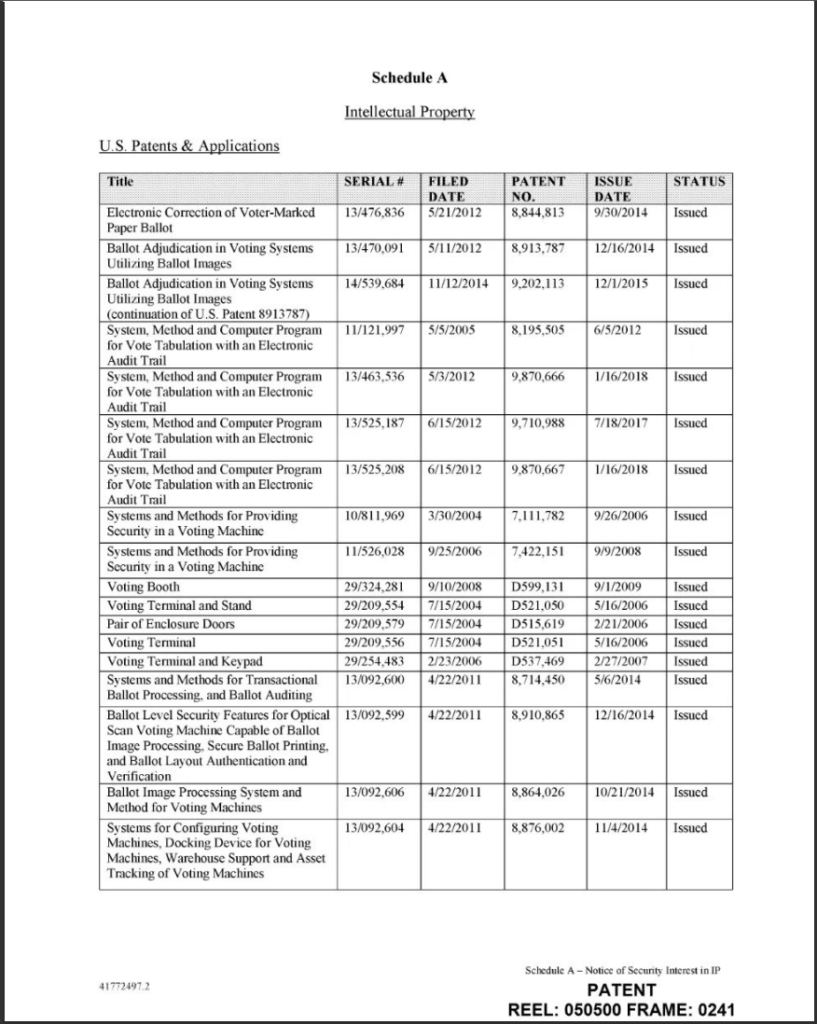
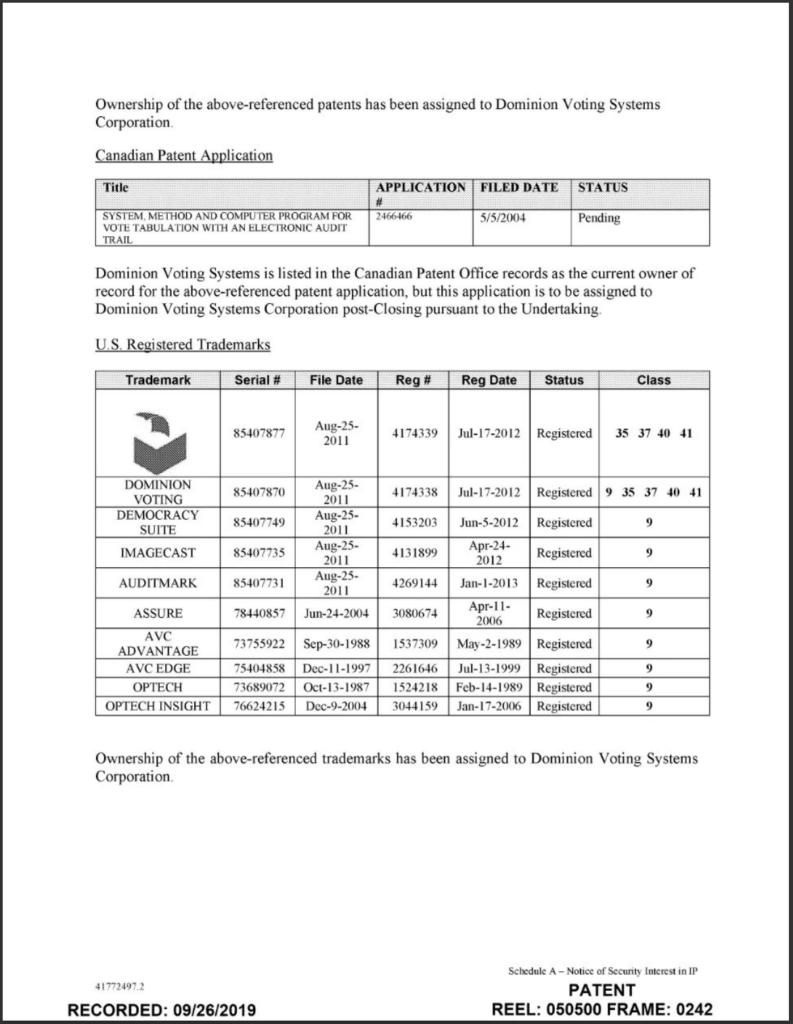



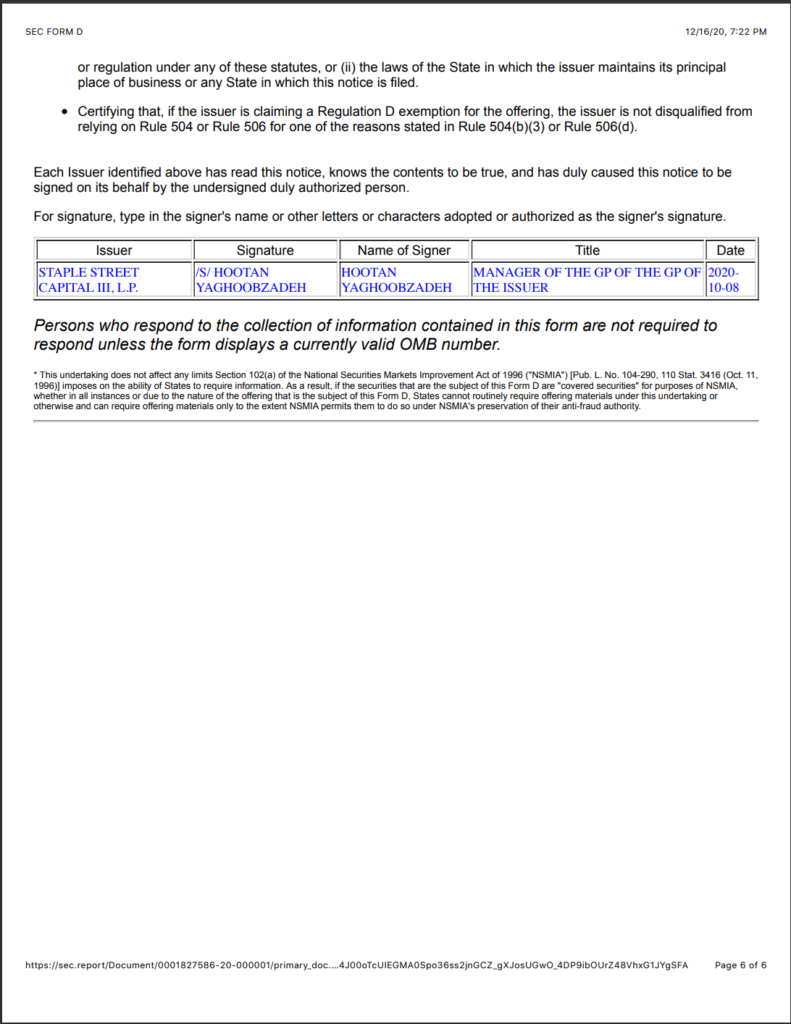
18. Dominion shares an address with Smartmatic in Barbados (see below)
19. Dominion data is seen going to their headquarters in Serbia and Toronto.
20. The following link analysis was gathered through open source methodologies and is easily verifiable.
21. As Dominion and Smartmatic makes claims that they are not connected in any way, not only are they connected but their business registration was in the same building on a foreign island to obfuscate their business dealings.
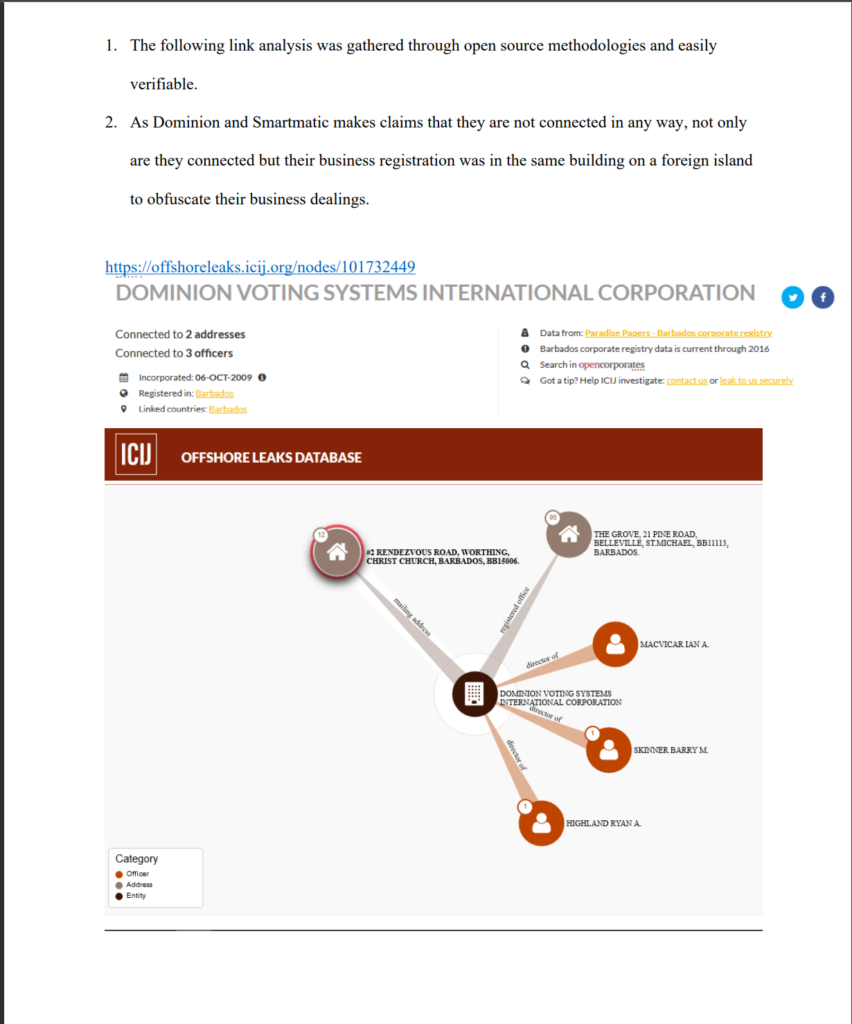
https://offshoreleaks.icij.org/nodes/101724285 Dominion Certificates
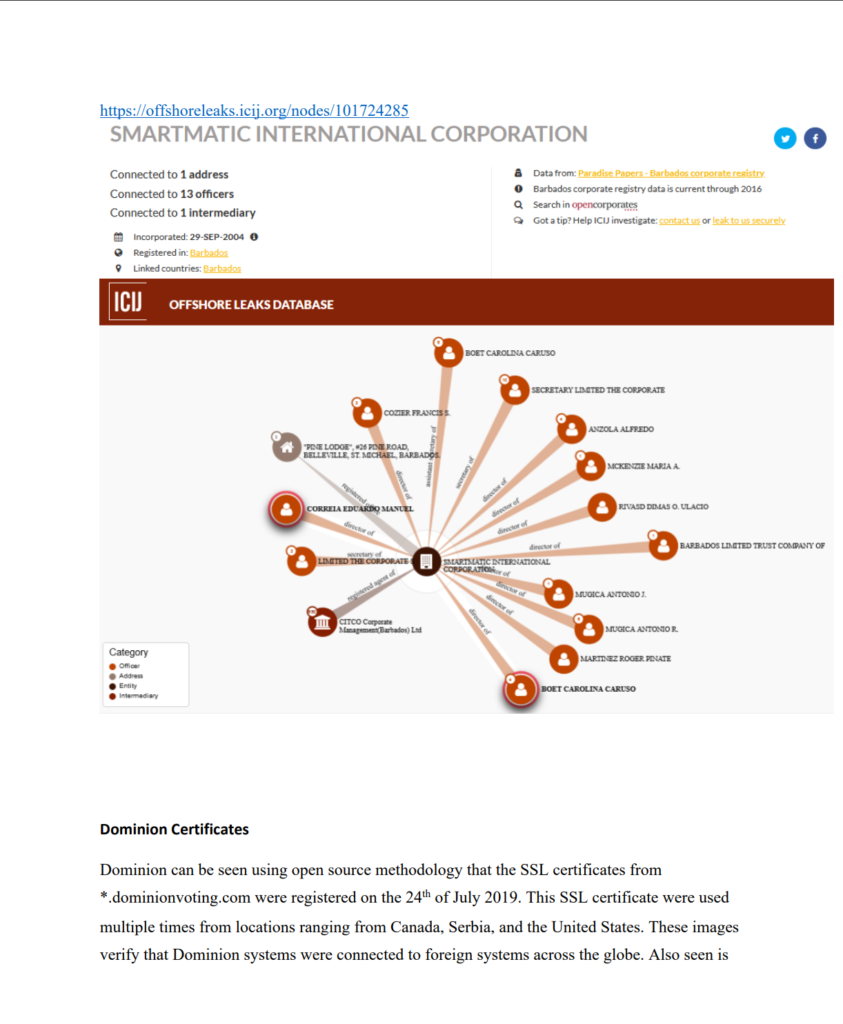
25. Dominion can be seen using open-source methodology that the SSL certificates from *.dominionvoting.com were registered on the 24th of July 2019. This SSL certificate were used multiple times from locations ranging from Canada, Serbia, and the United States. These images verify that Dominion systems were connected to foreign systems across the globe. Also seen is that the SSL certificate is used for the email server that was the same for the secure HTTP connections.
443.https.tls.certificate.parsed.fingerprint_sha256: 8f73a14d5f0fc10ebfa3086a99b9e7a550e822c71d762e627b73d12e5f1b8b9c
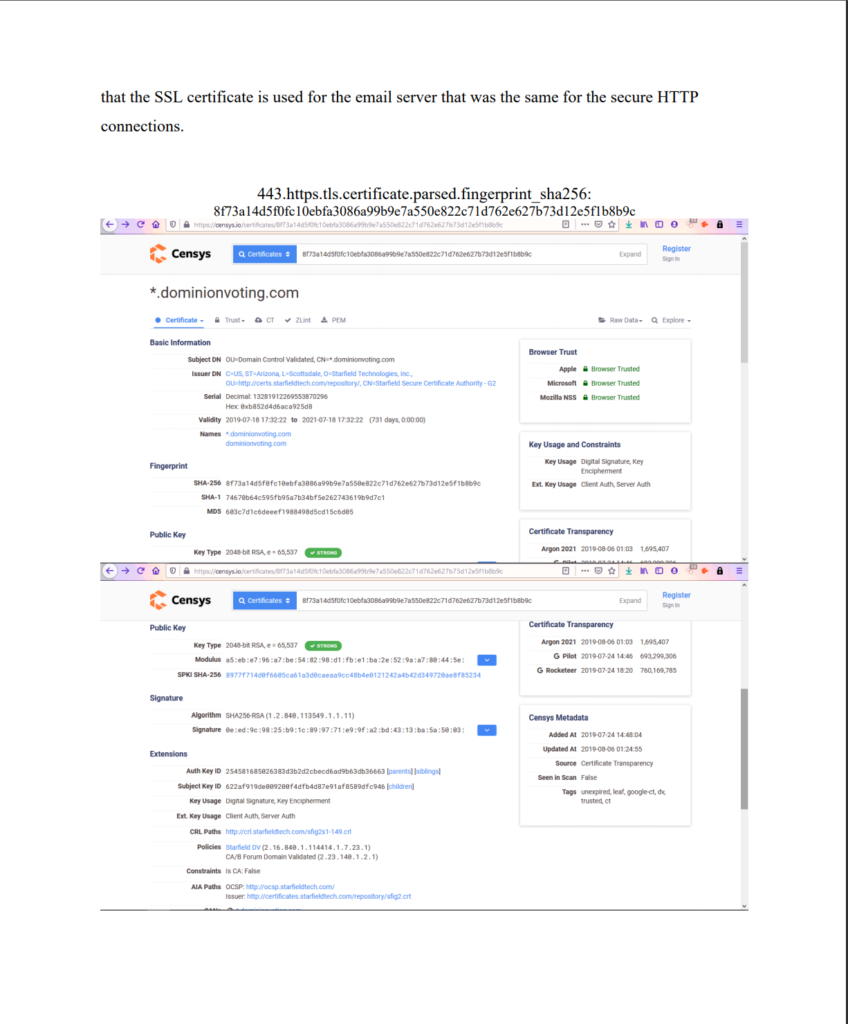
All share:
443.https.tls.certificate.parsed.fingerprint_sha256: 8f73a14d5f0fc10ebfa3086a99b9e7a550e822c71d762e627b73d12e5f1b8b9
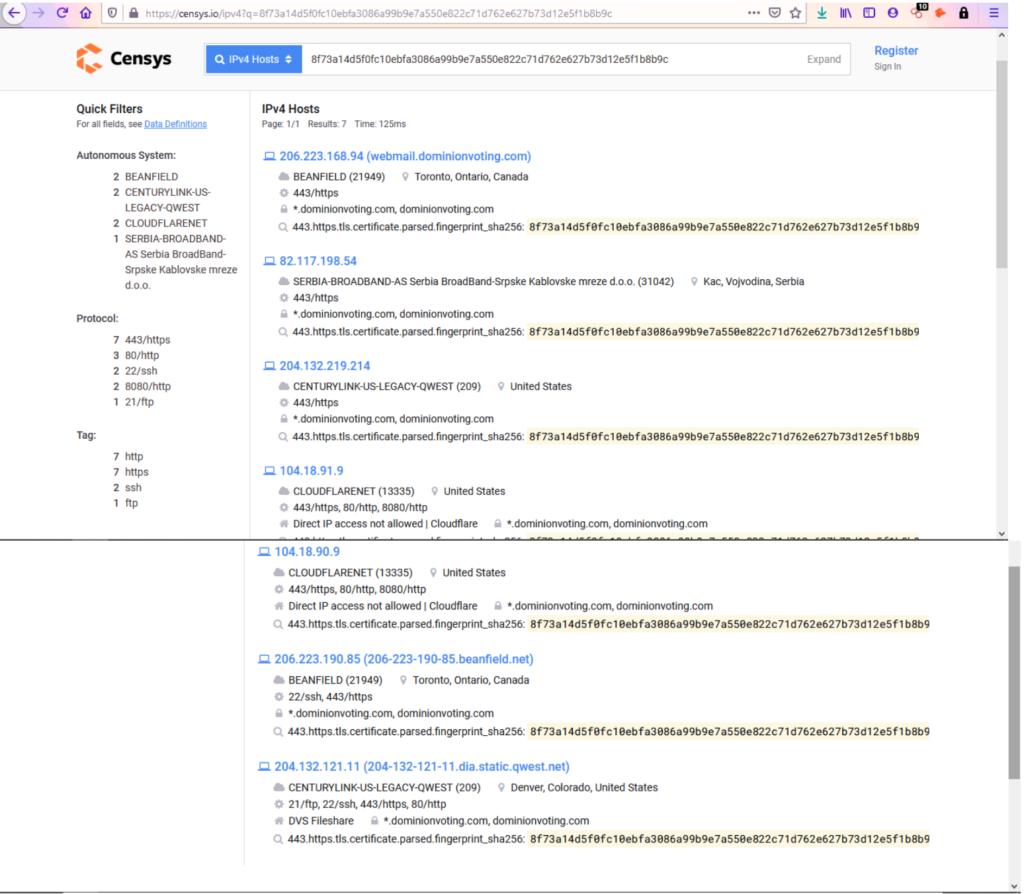
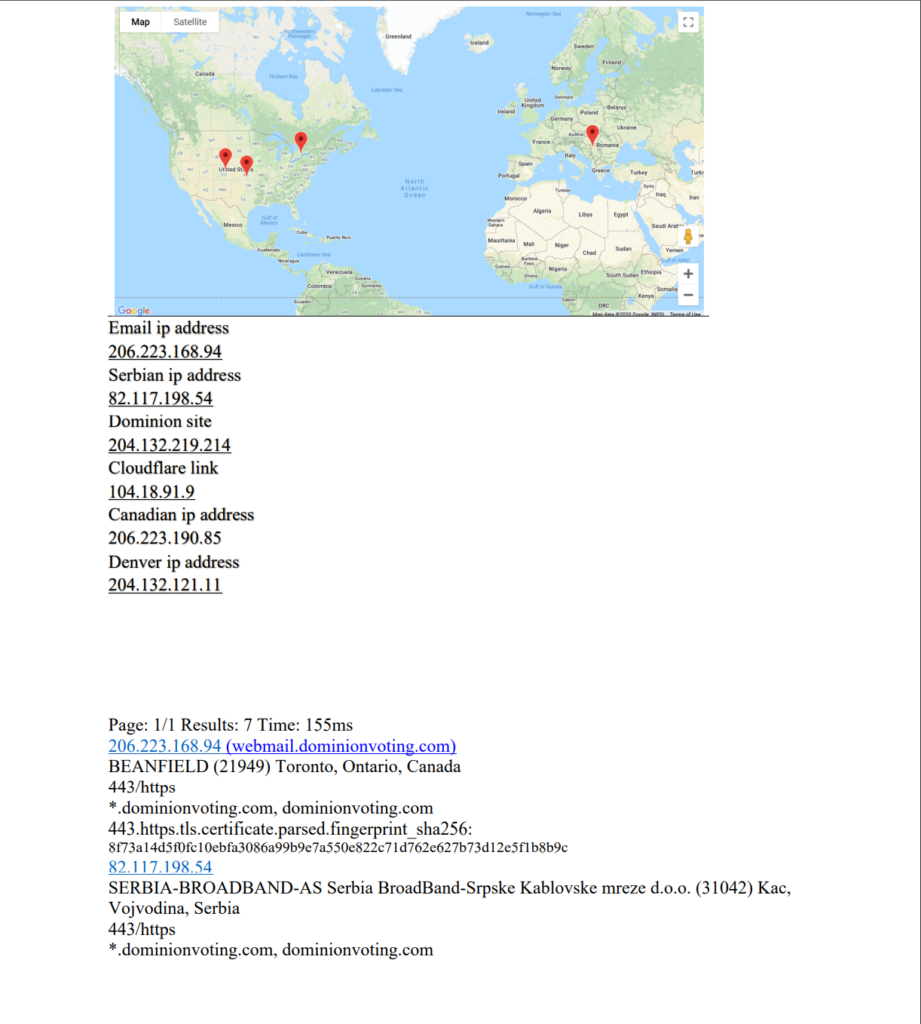
Email ip address: 206.223.168.94
Serbian ip address 82.117.198.54
Dominion site 204.132.219.214
Cloudflare link 104.18.91.9
Canadian ip address 206.223.190.85
Denver ip address 204.132.121.11
Page: 1/1 Results: 7 Time: 155ms
206.223.168.94 (webmail.dominionvoting.com)
BEANFIELD (21949) Toronto, Ontario, Canada
443/https
*.dominionvoting.com, dominionvoting.com
443.https.tls.certificate.parsed.fingerprint_sha256: 8f73a14d5f0fc10ebfa3086a99b9e7a550e822c71d762e627b73d12e5f1b8b9c 82.117.198.54
SERBIA-BROADBAND-AS Serbia BroadBand-Srpske Kablovske mreze d.o.o. (31042) Kac, Vojvodina, Serbia
443/https
*.dominionvoting.com, dominionvoting.com 443.https.tls.certificate.parsed.fingerprint_sha256: 8f73a14d5f0fc10ebfa3086a99b9e7a550e822c71d762e627b73d12e5f1b8b9c 204.132.219.214
CENTURYLINK-US-LEGACY-QWEST (209) United States
443/https
*.dominionvoting.com, dominionvoting.com 443.https.tls.certificate.parsed.fingerprint_sha256: 8f73a14d5f0fc10ebfa3086a99b9e7a550e822c71d762e627b73d12e5f1b8b9c 104.18.91.9
CLOUDFLARENET (13335) United States 443/https, 80/http, 8080/http Direct IP access not allowed | Cloudflare *.dominionvoting.com, dominionvoting.com 443.https.tls.certificate.parsed.fingerprint_sha256: 8f73a14d5f0fc10ebfa3086a99b9e7a550e822c71d762e627b73d12e5f1b8b9c 104.18.90.9
CLOUDFLARENET (13335) United States
443/https, 80/http, 8080/http Direct IP access not allowed | Cloudflare *.dominionvoting.com, dominionvoting.com 443.https.tls.certificate.parsed.fingerprint_sha256: 8f73a14d5f0fc10ebfa3086a99b9e7a550e822c71d762e627b73d12e5f1b8b9c 206.223.190.85 (206-223-190-85.beanfield.net)
BEANFIELD (21949) Toronto, Ontario, Canada
22/ssh, 443/https *.dominionvoting.com, dominionvoting.com 443.https.tls.certificate.parsed.fingerprint_sha256: 8f73a14d5f0fc10ebfa3086a99b9e7a550e822c71d762e627b73d12e5f1b8b9c 204.132.121.11 (204-132-121-11.dia.static.qwest.net)
CENTURYLINK-US-LEGACY-QWEST (209) Denver, Colorado, United States 21/ftp, 22/ssh, 443/https, 80/http DVS Fileshare *.dominionvoting.com, dominionvoting.com 443.https.tls.certificate.parsed.fingerprint_sha256: 8f73a14d5f0fc10ebfa3086a99b9e7a550e822c71d762e627b73d12e5f1b8b9c
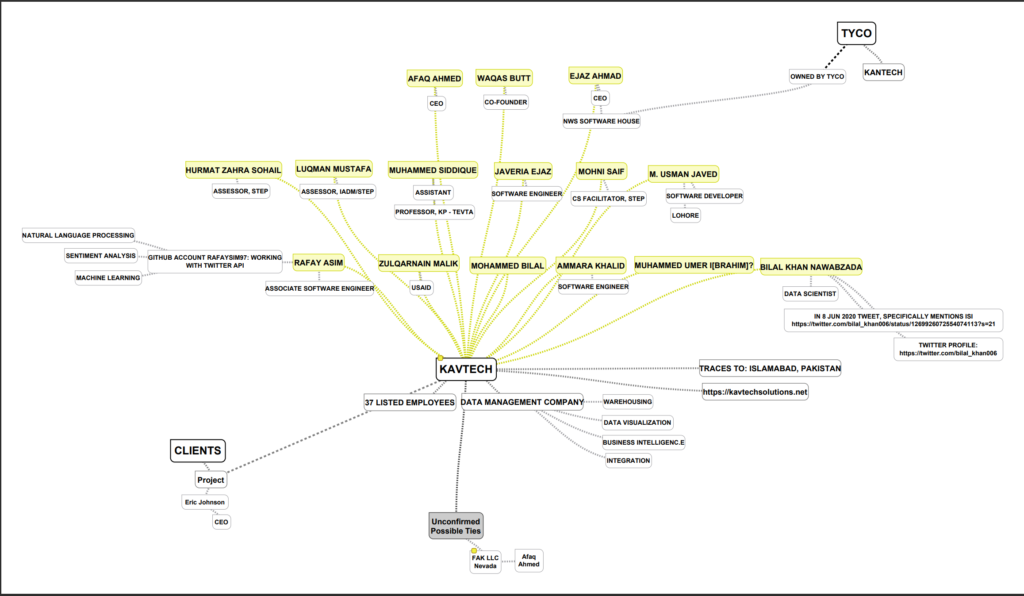
Kavtech
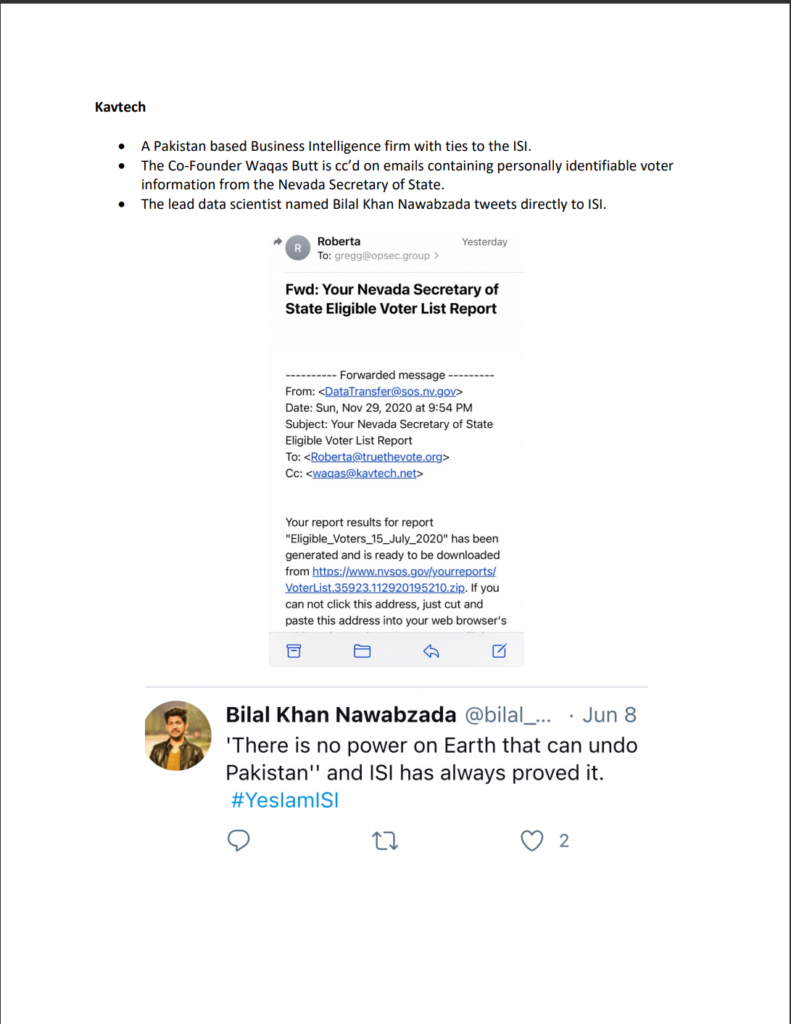
26. A Pakistan based Business Intelligence firm with ties to the ISI.
27. The lead data scientist named Bilal Khan Nawabzada tweets directly to ISI.
28. The Co-Founder Waqas Butt is cc’d on emails containing personally identifiable voter information from the Nevada Secretary of State.
a. This is a similar and deliberate act of unauthorized access of information and data as the hacking of the voter registration system by Iran. (E.O. 13800 of May 11, 2017)
29. Kavtech is a Pakistan based Business Intelligence firm with ties to the Pakistani intelligence ISI. The lead data scientist named Bilal Khan Nawabzada directly references Pakistani ISI in his social media.
30. Kavtech using Natural Language Processing and Sentiment Analysis to sway Voter opinion and intent to ultimately influence the election.
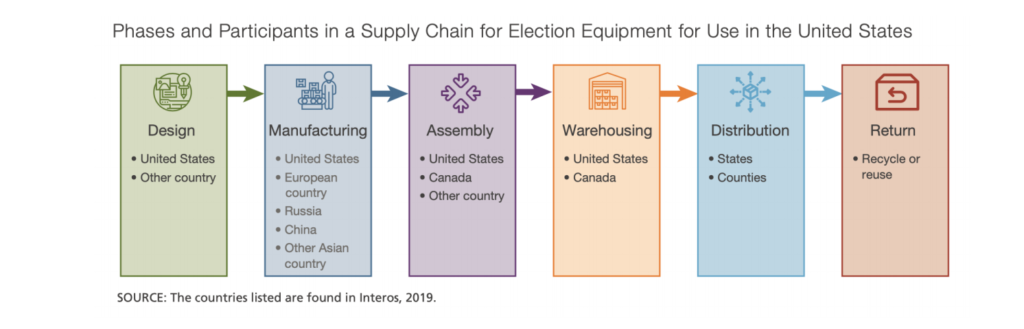
Supply Chain Concerns
31. One in five components used in voting machines are from China-based companies
32. On January 6, 2017 DHS Secretary Jeh Johnson on the Designation of Election Infrastructure as a Critical Infrastructure Subsector.
a. This means that election infrastructure becomes a priority within the National Infrastructure Protection Plan. It also enables this Department to prioritize our cybersecurity assistance to state and local election officials, but only for those who request it. Further, the designation makes clear both domestically and internationally that election infrastructure enjoys all the benefits and protections of critical infrastructure that the U.S. government has to offer. Finally, a designation makes it easier for the federal government to have full and frank discussions with key stakeholders regarding sensitive vulnerability information.
33. With that in mind, it is incredible that the Election equipment used in the November 3, 2020 election was manufactured in Russia, China and undisclosed Asian and European Countries (see below).
_________________________________
Reference:
Now I could go much further. My dolphin speakers have had time to go much further than you have reviewed so far in this chapter (what you have seen thus far was generally prepared by or before Thanksgiving, November 26, 2020).
But I’m hopeful, Dear Reader, that I have above shown you enough to win.

